缓冲区溢出漏洞是一种软件安全漏洞,当程序试图在缓冲区(用于临时保存数据的内存位置)中存储的数据超出其处理能力时,就会发生这种漏洞。 这种数据溢出会导致缓冲区溢出到相邻的内存中,这可能会破坏或覆盖其他重要数据,从而导致意外和潜在的恶意行为。 缓冲区溢出漏洞可用于执行任意代码、导致崩溃和导致拒绝服务攻击等。 开发人员在使用缓冲区时正确验证用户输入并正确分配内存以防止缓冲区溢出漏洞非常重要。
A buffer overflow vulnerability is a type of software security bug that occurs when a program tries to store more data in a buffer (a memory location used to hold data temporarily) than it can handle. This overflow of data can cause the buffer to overflow into adjacent memory, which can corrupt or overwrite other important data, leading to unexpected and potentially malicious behavior. Buffer overflow vulnerabilities can be used to execute arbitrary code, cause crashes, and cause denial-of-service attacks, among other things. It is important for developers to properly validate user input and properly allocate memory when working with buffers to prevent buffer overflow vulnerabilities.
了解漏洞
学习流程
Learning process
本次课程预计时间45+分钟
1. 演示漏洞入侵,并能造产生得影响
2. 认知了解 该漏洞相关
3. 介绍漏洞利用方法,产生漏洞原因
4. 了解漏洞相关编程和工具
5. 漏洞修复,安全加固
The estimated time of this course is 45+minutes
- Demonstrate vulnerability intrusion and its impact
- Understand the vulnerability
- Introduce vulnerability utilization methods and causes
- Understand vulnerability related programming and tools
- Vulnerability repair and security reinforcement
1.演示漏洞入侵
目标机:虚拟机Windows7,或同机房 Window7攻击使用系统工具:Linux,Windows || Python , metasploit-framework
Target machine: virtual machine Window7, or Window7 in the same machine room
The attack uses system tools: Linux, Windows | | Python, metasploit-framework
2.认知了解该漏洞相关
漏洞编号:CVE-2017-0143/0144/0145/0146/0147/0148
Vulnerability No.: CVE-2017-0143/0144/0145/0146/0147/0148
与以往不同,这次漏洞并不是公开披露在漏洞平台上,而是由黑客组织 Shadow broker 在2016年8月入侵了美国国家安全局旗下得方程式安全组织,并窃取了大量机密文件,后 Shadow broker组织公开说明已经入侵了方程式安全组织,但大部分人将信将疑,2017年4月14日夜间,该组织在多次出售无果,为表证明 Shadow broker组织抽取部分从方程式组织窃取来得黑客工具包公开披露在网上,一时间下载量猛增
Unlike in the past, this vulnerability was not publicly disclosed on the vulnerability platform, but was invaded by the hacker organization Shadow broker in August 2016, and stole a large number of confidential documents. Later, the Shadow broker organization publicly stated that it had invaded the equation security organization, but most people were skeptical. On the night of April 14, 2017, the organization sold many times without success, In order to prove that the hacker tool package extracted by Shadow broker organization and stolen from Equation organization was publicly disclosed on the Internet, and the download volume increased sharply at one time
在本次公开泄露部分方程式黑客工具包中,包含了大量恶意利用程序,和0day漏洞利用程序,一时间泄露大量漏洞,对互联网,PC设备产生极大安全隐患,其中包含了多个 Windows 远程漏洞利用工具,可以覆盖全球 70% 的 Windows 服务器,影响程度非常巨大。除Microsoft Windows以外,受影响的产品还有: IBM Lotus Notes,Mdaemon, EPICHERO Avaya Call Server,Imail。
In this public disclosure, the partial equation hacker toolkit contains a large number of malicious exploiters and 0day vulnerability exploiters. A large number of vulnerabilities are disclosed at one time, which will cause great security risks to the Internet and PC devices. It contains multiple Windows remote vulnerability exploiters, which can cover 70% of the world's Windows servers, with a huge impact. In addition to Microsoft Windows, the products affected include IBM Lotus Notes, Mdaemon, EPICHERO Avaya Call Server, and Imail.
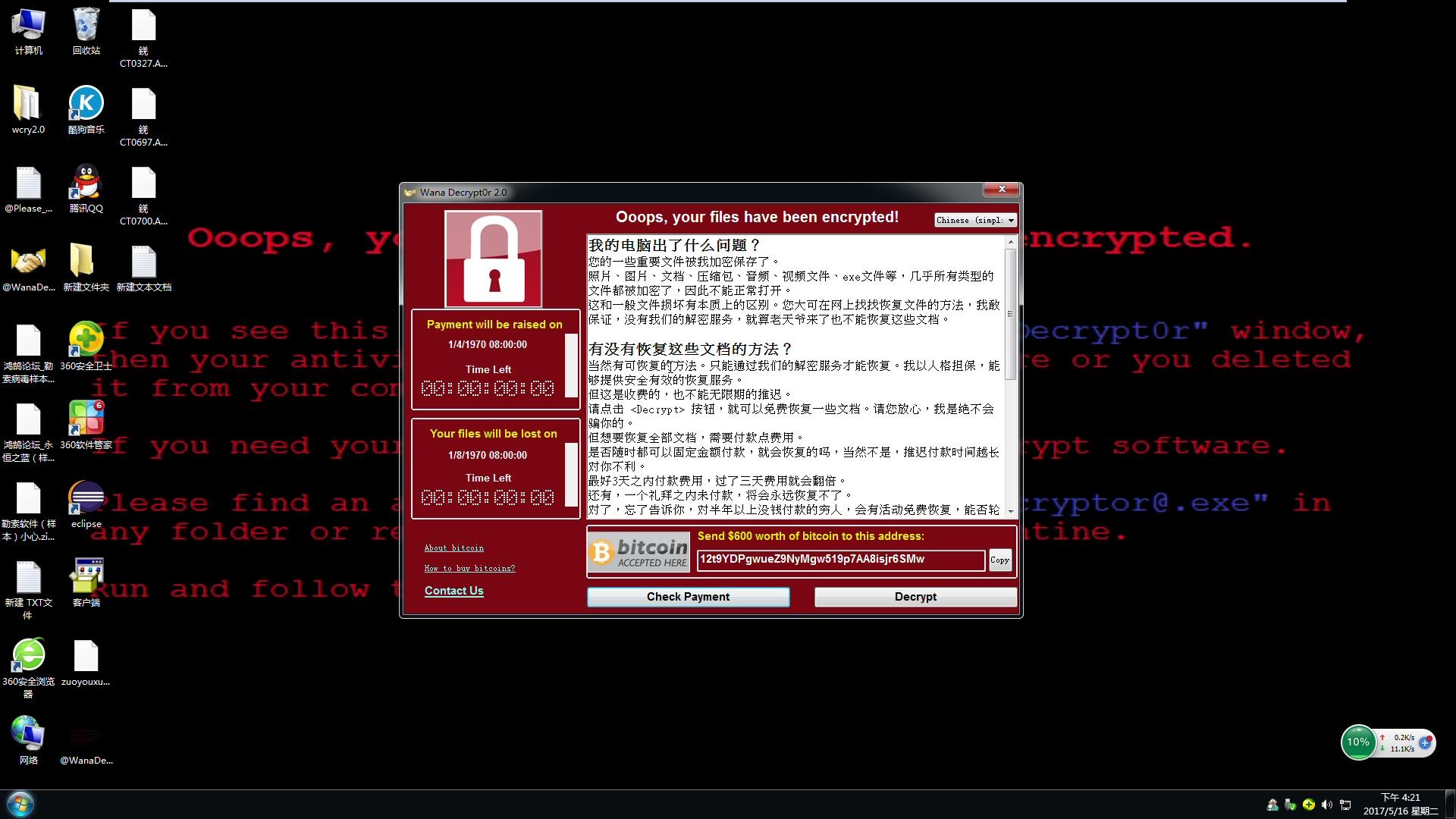
wannacry勒索病毒
5月12日,黑客通过改造该工具包漏洞利用程序,制作了wannacry勒索病毒,英国、俄罗斯、整个欧洲以及中国国内多个高校校内网、大型企业内网和政府机构专网中招,被勒索支付高额赎金才能解密恢复文件。,后续有黑客利用工具包泄露的漏洞,进行传播勒索病毒
On May 12, hackers created the wannacry blackmail virus by modifying the vulnerability exploitation program of the toolkit. Many universities and colleges in the United Kingdom, Russia, the whole Europe and China, as well as the intranet of large enterprises and private networks of government agencies were recruited, and they were blackmailed to pay a high ransom to decrypt and recover files., Later, hackers spread the blackmail virus by using the vulnerability disclosed by the toolkit
NSA网络攻击武器
本次泄露的部分,NSA漏洞工具包,开发时间还是在2012年
这些网络攻击武器工具包,只是美国安全局冰山一角,也就是NSA掌握大量未公开漏洞,网络攻击工具
NSA完全可以使用这些网络攻击工具控制计算机系统,或实行网络攻击
今年3月份,360安全团队,捕获到大量美国NSA安全局,使用量子攻击平台针对国内大量恶意流量
漏洞利用
使用Python ms17_010.py 脚本对目标进行攻击,执行恶意代码程序,后续上线到Msf,完全接管主机
漏洞分析
漏洞出现在Windows SMB v1中的内核态函数srv!SrvOs2FeaListToNt在处理FEA(File Extended Attributes)转换时,在大非分页池(内核的数据结构,Large Non-Paged Kernel Pool)上存在缓冲区溢出。函数srv!SrvOs2FeaListToNt在将FEA list转换成NTFEA(Windows NT FEA) list前会调用srv!SrvOs2FeaListSizeToNt去计算转换后的FEA lsit的大小。然后会进行如下操作
1.srv!SrvOs2FeaListSizeToNt会计算FEA list的大小并更新待转换的FEA list的大小
2.因为错误的使用WORD强制类型转换,导致计算出来的待转换的FEA list的大小比真正的FEA list大
3.因为原先的总大小计算错误,导致当FEA list被转化为NTFEA list时,会在非分页池导致缓冲区溢出
The vulnerability lies in the kernel state function srv in Windows SMB v1! SrvOs2FeaListToNt has a buffer overflow on the large non-paged pool (the data structure of the kernel, Large Non-Paged Kernel Pool) when processing the FEA (File Extended Attributes) conversion. Function srv! SrvOs2FeaListToNt will call srv before converting FEA list to NTFEA (Windows NT FEA) list! SrvOs2FeaListSizeToNt calculates the size of the converted FEA lsit. Then the following operations will be performed
1.srv! SrvOs2FeaListSizeToNt calculates the size of the FEA list and updates the size of the FEA list to be converted
- The calculated FEA list to be converted is larger than the real FEA list due to the incorrect use of WORD to force type conversion
- Because of the original total size calculation error, when the FEA list is converted to NTFEA list, the buffer overflow will occur in the non-paged pool
什么是缓冲区溢出?
What is a buffer overflow?
缓冲区溢出是一种非常普遍、非常危险的漏洞,在各种操作系统、应用软件中广泛存在。利用缓冲区溢出攻击,可以导致程序运行失败、系统宕机、重新启动等后果。更为严重的是,可以利用它执行非授权执行,甚至可以取得系统特权,进行各种非法操作。缓冲区溢出(buffer overflow),是针对程序设计缺陷,向程序输入缓冲区写入使之溢出的内容(通常是超过缓冲区能保存的最大数据量的数据),从而破坏程序运行、趁著中断之际并获取程序乃至系统的控制权。
Buffer overflow is a very common and dangerous vulnerability, which widely exists in various operating systems and application software. Buffer overflow attacks can lead to program failure, system downtime, restart and other consequences. What's more, it can be used to perform unauthorized execution, or even obtain system privileges for various illegal operations. Buffer overflow refers to writing overflow content (usually data that exceeds the maximum amount of data that can be stored in the buffer) to the program input buffer in response to the program design defect, thus damaging the program operation, taking advantage of the interruption and gaining control of the program and even the system.
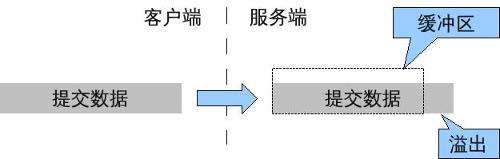
缓冲区溢出利用
Buffer overflow utilization
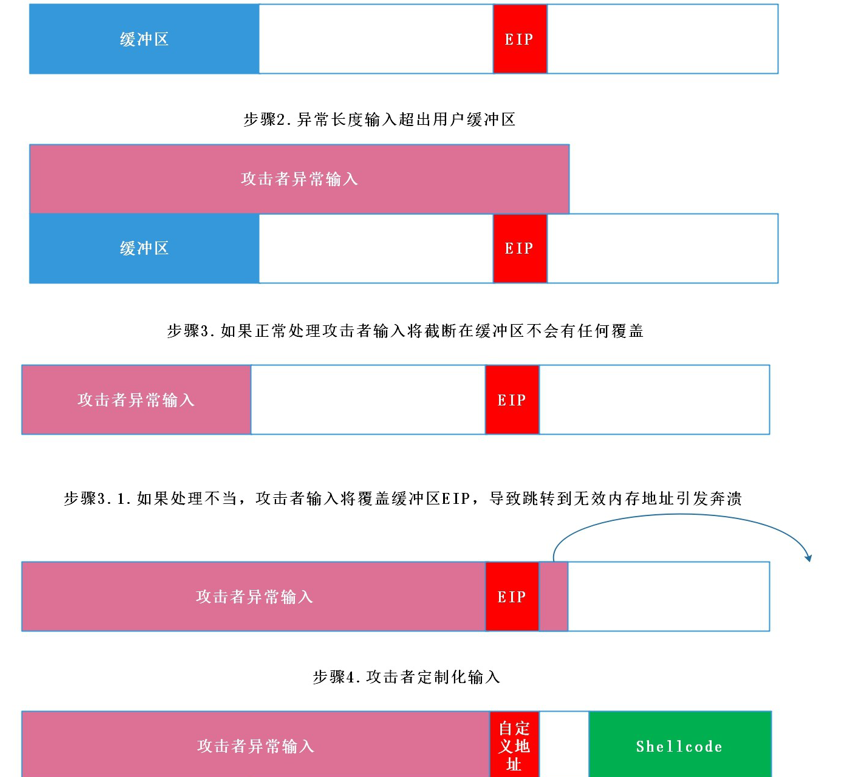
EIP是一个x86寄存器,但不是通用寄存器,原因是它里面存的值,是我们CPU下一次要执行的地址,CPU通过EIP寄存器,找到地址,去执行地址上的指令,通过缓冲区溢出 覆盖修改定制EIP值跳转到ShellCode完成恶意代码运行
EIP is an x86 register, but not a general-purpose register. The reason is that the value stored in it is the address of the next execution of our CPU. The CPU finds the address through the EIP register, executes the instructions on the address, and modifies the customized EIP value through buffer overflow to jump to ShellCode to complete the malicious code operation
某游戏服务器 缓冲区溢出漏洞
Buffer overflow vulnerability of a game server
服务器会监听一个 udp 11011端口,用于游戏客户端通信,向这个端口发送数据包,0x01,0x00,0x80。只有3个字节,服务器就会马上崩溃退出,这里是直接崩溃,也可以导致恶意代码执行完全控制服务器
The server will listen to a udp 11011 port for game client communication and send data packets to this port, 0x01,0x00,0x80. With only 3 bytes, the server will immediately crash and exit. Here is a direct crash, which can also cause malicious code execution to completely control the server
漏洞分析
Vulnerability analysis
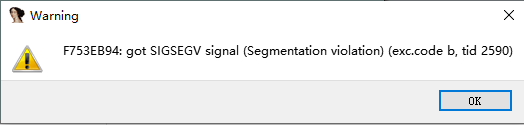
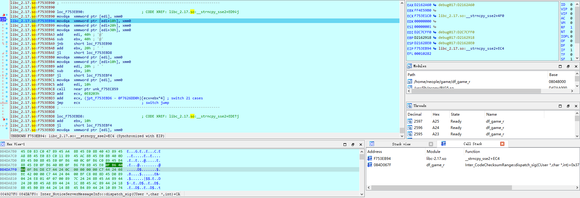
IDA远程附加调试可以看到,发送漏洞数据 程序发生了段错误,问题出在strncpy函数,在写入一个不存在的地址
IDA remote additional debugging can see that a segment error occurred in the program sending vulnerability data. The problem is that the strncpy function is writing a non-existent address
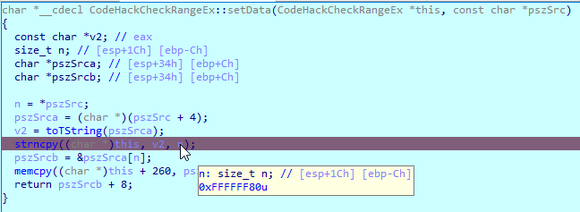
可以看到程序调用strncpy函数时,长度参数0xFFFFFF80,这个长度显然是不正常的
You can see that when the program calls the strncpy function, the length parameter 0xFFFF80 is obviously abnormal. You can see that when the program calls the strncpy function, the length parameter 0xFFFF80 is obviously abnormal
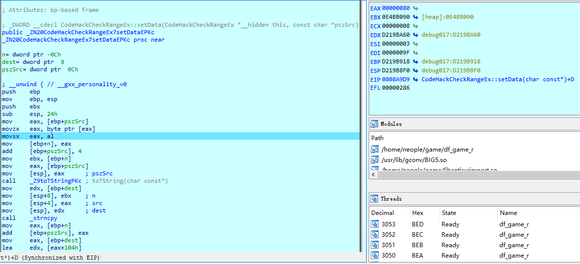
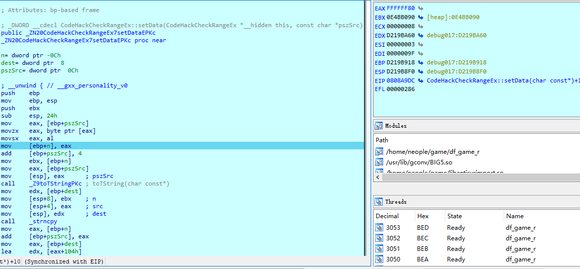
看下汇编代码,程序先从内存中把1字节的0x80取出放在寄存器,然后执行了movsx指令,把al赋值给了eax,这是一条有符号的赋值指令,如果al为负,则eax就会为负,如果al的值是0x7F,赋值后,eax就是0x7F,但是al的值是0x80,因为有符号的原因,实际上是-127,赋值后eax就会变成-127,实际值为0xFFFFFF80,而strncpy的长度参数可是无符号的,所以0xFFFFFF80在strncpy看来就是一个很大的数,然后直接把数据写到尽头,发生段错误
0x80 是十进制 -128,不是一个Ascii字符,也无法显示成一个符号,一般会显示成为空或问号,会导致程序报错
Look at the assembly code. The program first takes a byte of 0x80 from memory and puts it in a register. Then it executes the movsx instruction and assigns al to eax. This is a signed assignment instruction. If al is negative, eax will be negative. If al is 0x7F, eax will be 0x7F after assignment, but the value of al is 0x80. Because of the sign, it is actually - 127. After assignment, eax will become - 127, and the actual value is 0xFFFF80, The length parameter of strncpy is unsigned, so 0xFFFFFF80 is a large number in strncpy's view, and then directly writes the data to the end, causing a segment error
0x80 is a decimal - 128, not an Ascii character, nor can it be displayed as a symbol. Generally, it will be displayed as a blank or question mark, which will cause the program to report an error
Let's talk about the idea. The target of strncpy writing is the stack, and the length is controllable. That is the classic buffer overflow vulnerability. If the length is long enough to cover the return pointer of the function, the program can be directly controlled. If the data is carefully constructed, the program can complete a series of operations, achieving the effect of remote command execution
谈下思路,strncpy写入的目标是栈,且长度可控,那么就是经典的缓冲区溢出漏洞,如果长度足够长可以覆盖函数的返回指针,那么就能直接控制程序,如果数据再经过精心构造,就能使程序完成一系列操作,达到远程命令执行的效果
Let's talk about the idea. The target of strncpy writing is the stack, and the length is controllable. That is the classic buffer overflow vulnerability. If the length is long enough to cover the return pointer of the function, the program can be directly controlled. If the data is carefully constructed, the program can complete a series of operations, achieving the effect of remote command execution
问题出处
The source of the problem
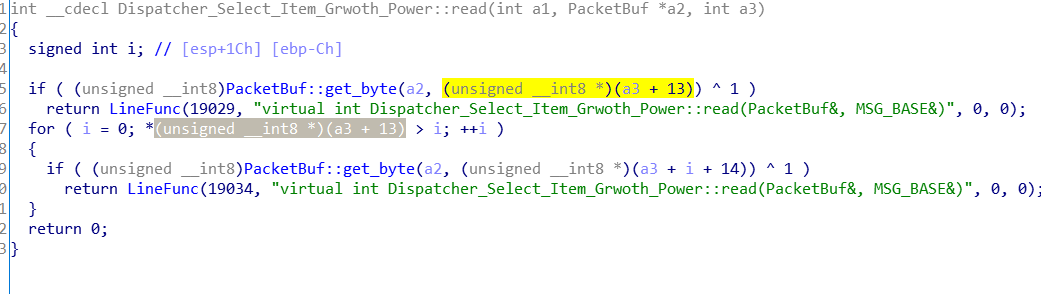
在 Dispatcher_Select_Item_Grwoth_Power::read函数,服务端接受到客户端发来得数据包抽取1字节来作为for循环的次数,没有对循环次数任何限制,可导致客户端自定义循环次数进入循环之后数据包中循环读取字节并写入到变量a3,后返回数据
In Dispatcher_ Select_ Item_ Grwoth_ Power:: read function. The server receives the data packet sent by the client and extracts 1 byte as the number of for cycles. There is no limit on the number of cycles, which can cause the client to define the number of cycles to enter the cycle. After that, the bytes are read in the data packet and written to the variable a3, and then the data is returned
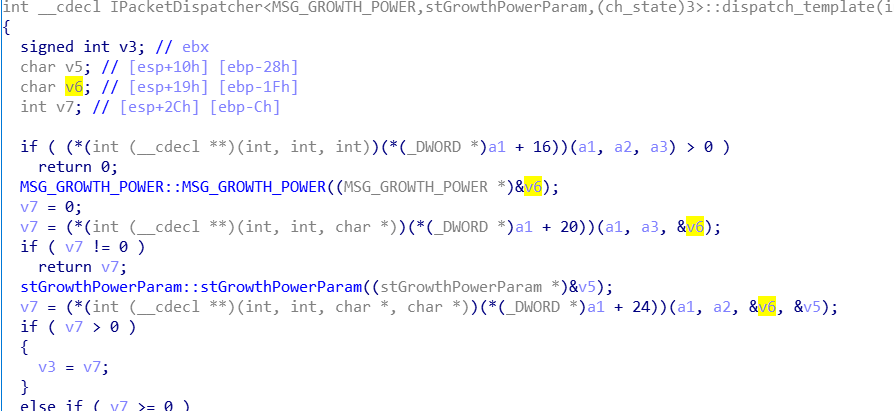
最后被函数:IPacketDispatcher<MSG_GROWTH_POWER,stGrowthPowerParam,(ch_state)3>::dispatch_template调用并将恶意数据存放到v6变量,v6默认开辟大小19字节,恶意数据大小已经超过19,导致溢出覆盖
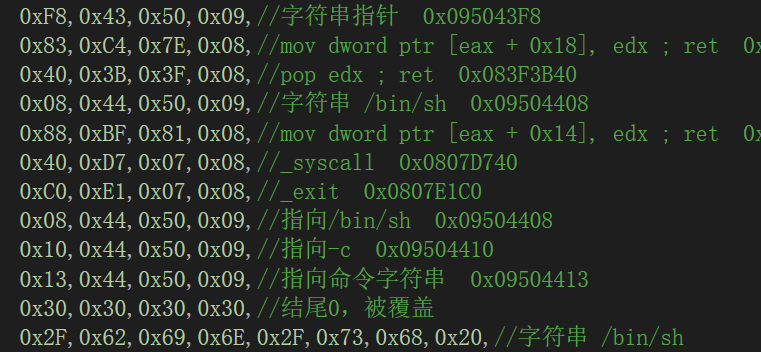
先有漏洞攻击程序,ff为255次循环后填充a造成缓冲区溢出,后覆盖内存地址跳转至syscall调用执行execve函数,导致恶意命令被执行
Finally, the function: IPacketDispatcher<MSG_ GROWTH_ POWER,stGrowthPowerParam,(ch_state)3>::dispatch_ Template calls and stores malicious data in v6 variables. The default size of v6 is 19 bytes. The size of malicious data has exceeded 19, resulting in overflow coverage
There is a vulnerability attack program first. ff is 255 cycles, then fill a buffer overflow, and then overwrite the memory address and jump to syscall to execute the execve function, resulting in the execution of malicious commands